About RiskFinder
RiskFinder is a web service for diagnosing vulnerabilities in Android mobile apps.
No knowledge of development is required.
The diagnosis results are obtained instantly using only the application file and a browser.
This is a valuable service for assisting in the prevention of security incidents.
Features
- Can be used by anyone by simply uploading the file using a browser
- Diagnosis is possible using only the application file -- No source code is needed
- Because RiskFinder is a web service, the latest version is always available
- In addition to vulnerabilities, RiskFinder also detects quality-related items and items easily mistaken for malware
- Outputs information compliant with the "Smartphone Privacy Initiative" issued by the Ministry of Internal Affairs and Communications (MIC)
Background
The rapid spread of Android mobile devices has led to the release of a large number of Android applications today. However, this sudden growth in the Android market has caused a shortage of technicians who are proficient in the Android platform. In many cases, technicians with insufficient experience are involved in development, mobile applications are developed in a shorter timeframe than conventional applications, and upgrades are released on a short cycle so that development tends to be focused on continually moving ahead. As a result, many apps have been released with security holes (vulnerabilities) and have components that make them easily mistaken for malware. Releasing applications with these problems can harm the corporate image and incite problems, and in the worst case, can even lead to security incidents.
Despite these types of problems, there are still few experienced developers, and so orders must sometimes be placed with developers having insufficient technical ability. However, an in-depth knowledge of security is required to find security holes and quality issues during the acceptance test conducted by customers, and as a result, it is typically extremely difficult for customers to find all possible issues.
Development History
At Taosoftware, we have built a vast technological knowledge base while conducting R & D since the Android OS was launched. At the same time, and we have been committed to expanding awareness of security issues among developers by providing information through our blog, lectures, and other communication platforms.
- tSpychecker for application privilege issues tSpychecker
- tPackageExplorer for verifying the application structure tPackegeExploer
- tPacketCapture for verifying the application communication content tPacketCapture
In January 2012, Impress Japan published our book for programmers, Android Security: Developing Secure Applications (in Japanese).
In the course of delivering lectures and holding consultations about security,
we often heard that it was difficult for everyone from developers to outsourcers to be fully aware of the technical information about security,
and tracking the security items that are constantly added and modified by Android updates was an arduous task. We were often asked if a system was available enabling easy diagnosis of application security.
In response to these requests, we developed RiskFinder based on the concept of enabling easy accessibility by automating valuable security checks.
RiskFinder can be used to enable easy diagnosis of vulnerabilities for ensuring that applications maintain stable quality.
Usage Procedure
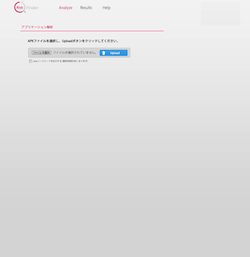
A report is created by simply uploading the APK file using a browser.
- Upload the APK file (screen at bottom left)
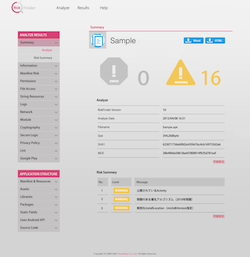
- Open the analysis results (screen at bottom right)
Features
1. Can be used by anyone by simply uploading the file using a browser
Diagnosis of vulnerabilities using source code requires a compiler and other development environments and tools, and users must have some knowledge of development. With RiskFinder, there is no need to obtain any tools beforehand, and anyone can immediately run a diagnosis for vulnerabilities.
2. Diagnosis is possible using only the application file -- No source code is needed
With RiskFinder, diagnosis can be performed even when you cannot obtain the source code or the source code for the specific application version is unknown. Diagnosis is also conducted simultaneously for the libraries (such as advertising modules) that the application is using.
3. Because RiskFinder is a web service, the latest version is always available
The Android OS is updated frequently. RiskFinder is also constantly updated to keep pace with the latest information for the Android. Because RiskFinder is a web service, the latest version is always available to the customer. (For inquiries about installing this service on company networks, please contact us.)
4. In addition to vulnerabilities, RiskFinder also detects quality-related items and items easily mistaken for malware
We often see cases where incorrect code on the Internet was simply copied and used. Because developers do not have enough knowledge of the Android platform, they often assign unnecessary permissions or include unnecessary functions so that the application is mistaken for malware. RiskFinder also conducts these types of quality checks on the application.
5. Outputs information compliant with the "Smartphone Privacy Initiative" issued by the Ministry of Internal Affairs and Communications (MIC)
Information is provided for creating an application compliant with the MIC's "Smartphone Privacy Initiative" so that users can use it with peace of mind. This supports developers in creating applications that take into account the privacy policy protection of users.
6. Developed by a company specializing in the Android platform
Taosoftware Co., Ltd. is an established Android application development company in Japan that has been conducting R&D on the Android since its initial launch by Google. Our operations are currently devoted exclusively to Android, and we conduct both contracted development and R&D by tapping into our extensive tried-and-tested knowledge base. We constantly keep up to date on the latest Android information, and we also incorporate the latest OS information in RiskFinder.
Usage Examples
- Application ordering
- Application development
- Determination of in-house applications (MDM)
- Application websites and publications
Application ordering
When application development is subcontracted outside the company, the customer placing the order is responsible for testing of the delivered application.
When the customer placing the order does not have development expertise, the customer can test application operations from the user standpoint but cannot easily test for vulnerabilities, user privacy protection, and other issues. This type of testing requires an in-depth knowledge of the Android platform.
The diagnostic report provided by RiskFinder can be used to enable precise communication between the developing company about vulnerabilities and privacy protection for allowing release of an application that can be used with peace of mind by users.
Application development
In many cases, requirements for security and user privacy protection are not clearly defined in the requirements specification. In these types of situations, security and privacy protection may or may not be implemented depending on the knowledge and experience of the people involved in development.
RiskFinder can be used to diagnose vulnerabilities during development or before delivery for enabling the creation of applications with stable quality regardless of the level of the developers.
The RiskFinder report can also be used in the delivery package as a testing record for vulnerabilities and privacy protection.
Determination of in-house applications (MDM)
If an application is used within the company for mobile device management (MDM), verification that the selected application is not malware is required. Testing using virus check software detects applications that are clearly malware, but it does not detect applications that fall into the gray zone (software that uses the private information of users, but it is unclear if it is being used for legitimate purposes). These tests also do not warn that the application is in the gray zone.
RiskFinder can be used to diagnose applications for enabling detection of gray-zone applications and providing helpful information in determining whether an application should be used.
Application websites and publications
Published content in application websites and books can be tremendously influential to users.
When an application is introduced on a website or publication, it is assumed to be a safe application and is adopted by many users. However, there have been cases where websites and publications have inadvertently introduced malware.
Recently, attention has been focused on the problem of gray-zone applications, and even the Ministry of Internal Affairs and Communications (MIC) has expressed concern about the use of smartphone user information. For people who operate these websites or edit publications, it is essential to verify that the posted applications are safe and secure. RiskFinder can be used to diagnose applications for finding out what type of application it is and preventing the inadvertent introduction of malware and gray-zone applications.
Basic Functions
- Login and logout functions
- Analysis results verification function
- Past analysis results management function
- Analysis results download (Word, HTML format) function
- Java source code output function by reverse engineering
Analysis Functions
Static analysis is conducted on the application, and the results are output in report form. The detection results are displayed on a list on the summary page.
Categories
The information is categorized by detection type into Manifest Risk, Permission, File Access, String Resources, Logs, Network, Module, Cryptography, Secure Logic, Privacy Policy, and more, for displaying detailed results.
Risk Levels
The risk level of the detection results is classified as ERROR, WARNING, CONFIRM, or INFO.
Detection Results Messages
Detection results messages are provided in three blocks: Detection details, detection reason, and remedy. The report includes the specific remedy procedure for providing an easy-to-understand way of resolving the problem.
Detailed Analysis Results Manual
Detailed explanations about the detection results are included in the Analysis Results Manual
Detection Items
In addition to application vulnerabilities, a check is also conducted for items that can be easily mistaken for malware and for bugs and other deficiencies that harm quality. Testing is available for more than 500 diagnostic items. Some of the diagnostic items are shown below.
Examples of detection items for security
- Report on vulnerabilities in activities
- Report on vulnerabilities in services
- Report on vulnerabilities in content provider
- Report on vulnerabilities in broadcast receiver
- Analysis of AndroidManifest.xml and report on vulnerabilities
- Detailed descriptions of permissions that are used
- Report on permissions that cannot be used
- Report on permissions that are not needed
- Report on access to external storage device
- Report on use of MODE_WORLD_READABLE/MODE_WORLD_WRITEABLE
- All character strings included in the program can be output for verifying that they do not contain any secure information.
- Report on log output
- Report on Web View where JavaScript can be used
- Report on HTML files within assets where JavaScript is used
- Detection of URLs contained in program for enabling verification of communication routes that are unencrypted.
- Detection of URLs contained in program for enabling verification that access was not performed to unneeded servers.
- Detection of encryption logic for enabling verification that encryption with a low level of security is not being used
- And report on many other items pertaining to vulnerabilities
Examples of detection items that could be mistaken for malware
- Permission combinations are determined for report on whether the software is a gray-zone application。
- Providing of suggested workarounds if dangerous permissions are being used
- Report on advertising libraries that are being used
- Libraries contained in the program are detected for reporting on any dangerous libraries
- Report on gray-zone libraries that are being used
- And report on many other items of attention
Examples of detection items for quality
- Enables confirmation for whether certificates are properly included
- Reports on unnecessary items in AndroidManifest.xml
- Reports on old code performing "sdcard" access to external storage devices
- The image files contained in the program are verified for checking that there are no license violations
- Libraries contained in the program are detected for verifying any license violations
- Report on spelling mistakes in character literal
- Report on possibility that an error occurs during execution
- Report on deviations from recommended Android rules
- And report on many other items pertaining to quality
Other Topics
License Types
RiskFinder can be installed under a server license, on Amazon Web Services, or on an in-house server.
Prices
Actual prices vary depending on customer's specific usage, including the number of users, number of analyzed applications (including unlimited), license period, and supported items, and so please inquire for details.
Web Site
About the details, please check the RiskFinder site .
